 In preparation for an upcoming project with my resident Code Monkey, I decided it was time to link the lab to my vCloud Air instance using a VPN. However as GUI access to the firewalls are disabled in the lab, the on-premises configuration will have to be done using the CLI.
In preparation for an upcoming project with my resident Code Monkey, I decided it was time to link the lab to my vCloud Air instance using a VPN. However as GUI access to the firewalls are disabled in the lab, the on-premises configuration will have to be done using the CLI.
In the following example I assume you have configured a default routed network on vCloud Air, and have also deployed an Edge Gateway.
vCloud Air
In this example, I am using the following details (substitute accordingly):
- Public IP: 92.246.244.211
- Local network: 192.168.109.24/24
- Peer network: 10.10.10.0/24
Connect to your vCloud Air instance and select Gateways. You should have already assigned a public IP:

Click Manage in vCloud Director.
An Edge Gateway should already be defined. Right-click and select Edge Gateway Services…
Click on the VPN tab.
Check the box Enable VPN and click Public IPs…
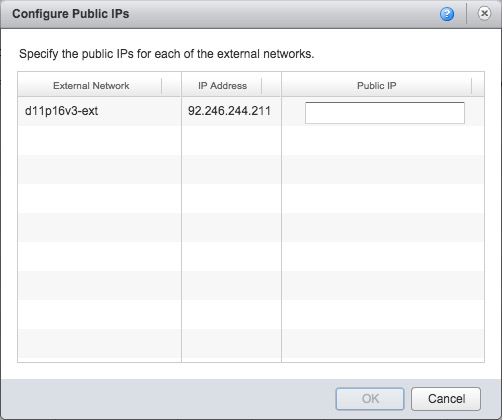
Type the public IP shown into the box and click OK.
In the Configure Services: gateway box, click Add…

Type a name in the Name box, and select a remote network from the Establish VPN to drop-down box.
Click to select the local network, and then type the network address of your on-premises network in CIDR notation in the Peer Networks box.
In the Local ID box, type the public IP of your Edge Gateway (in my case 92.246.244.211):

In the Peer ID box, type the public IP of your firewall (in my case a Cisco ASA). Type the same IP address in the Peer IP box.
Finally, click the Show key box and make a copy of the pre-shared key.
Click OK, and then OK again. If configured correctly, the settings should look like:

Note: I have blanked out my peer ID and IP for security reasons.
Cisco ASA configuration
In this example, I am using the following details (substitute accordingly):
- Local network: 10.10.10.0/24
- Peer network: 192.168.109.0/24
Access the ASA’s command line interface. Enter configuration mode, create objects for the local (on-prem) and remote (vCloud Air) networks and an access list for the traffic:
conf t object network net_vca subnet 192.168.109.0 255.255.255.0 object network net_localnet subnet 10.10.10.0 255.255.255.0 access-list local_to_vca line 1 extended permit ip 10.10.10.0 255.255.255.0 192.168.109.0 255.255.255.0
Create a group policy for the VPN using your vCloud Air public IP:
group-policy 92.246.244.211 internal group-policy 92.246.244.211 attributes vpn-tunnel-protocol ikev2 ikev1 exit
Configure the tunnel group properties:
tunnel-group 92.246.244.211 type ipsec-l2l tunnel-group 92.246.244.211 general-attributes default-group-policy 92.246.244.211 tunnel-group 92.246.244.211 ipsec-attributes
Configure the pre-shared key, using the one copied earlier from vCloud Air:
ikev1 pre-shared-key abcdefghijklmnopqrstuvwxyz12345678 ikev2 local-authentication pre-shared-key abcdefghijklmnopqrstuvwxyz12345678 ikev2 remote-authentication pre-shared-key abcdefghijklmnopqrstuvwxyz12345678
Define the keepalive:
isakmp keepalive threshold 10 retry 2
Configure the crypto map entries:
crypto map outside_map 1 match address local_to_vca crypto map outside_map 1 set peer 92.246.244.211 crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 crypto map outside_map 1 set ikev2 ipsec-proposal DES 3DES AES AES192 AES256 crypto map outside_map 1 set pfs group2
The vCloud Air Edge Services Gateway supports Triple-DES as a minimum, but if your ASA supports AES-256 then the above transform set can be tightened up a bit.
Lastly, configure NAT:
nat (inside,outside) source static net_localnet net_localnet destination static net_vca net_vca no-proxy-arp route-lookup
vCloud Air firewall rules
The last thing to do is to enable the firewall rules on the vCloud Air side to allow traffic to pass from our on-premises network to the default-routed-network (and vice-versa).
As this is a lab environment, I plan to allow the following:
- TCP/UDP in & out
- ICMP in & out
In total that should be four rules.
Back in vCloud Director, select your vDC and then click on the Edge Gateways tab. Right-click the gateway and click Edge Gateway Services. Next, click on the Firewall tab.
Check the Enable firewall box, then click Add…

Enter a name for the rule, and specify the Source as the default-routed-network subnet in CIDR notation:

In the Destination field, specify your on-premises subnet. Select TCP & UDP from the Protocol drop-down box:
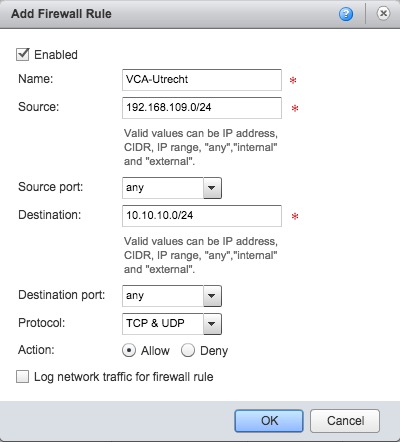
Click OK.
Repeat the above steps for the remaining rules. Once done, the rules should look something like this:

Lastly, click OK.
You should now be able to pass traffic between your on-premises network and your vCloud Air network.
Pingback: Wednesday Tidbit: Using VCA-CLI to manage vCloud Air | virtualHobbit
Nice article, I remember struggling with this a year ago when I implemented vCA at the company I work for. I’d be interested to see what it would look like with VPN failover – i.e. I have two ISPs on site and setting up vpn failover between both of those ISPs to vCA. I haven’t figured that part out yet.
LikeLike
Hey, Nice Article.
However, i have a scenario, my customer wants to create redundant VPN, like we do in Cisco ASA. So, they have two internet links on their end, Say internet A and Internet B. They connect to us. Say Internet C. So they want to create a Single VPN between A to C and if in case A to C goes down, then Tunnel B to C should come up.
Some thing like in ASA – Crypto map X peer A.A.A.A B.B.B.B to be configured on internet C.
C is a Edge Firewall with IPsec Services enabled.
Any suggestions how can we achieve that?
LikeLike
Pingback: The vSAN Witness Appliance in vCloud Air: Part 3 (Network) – Jase's Place